Introduction
In an era where digital security is paramount, Two-Step Verification (2SV) has emerged as an indispensable measure for safeguarding online accounts. Google, a global technology leader, offers this robust security feature to protect its users from unauthorized access and online fraud.

Benefits of 2SV
Implementing 2SV provides numerous benefits for Google users:
- Enhanced Account Protection: 2SV adds an extra layer of security by requiring users to provide both their password and a unique verification code when logging in to their Google accounts. This makes it significantly more difficult for unauthorized individuals to gain access.
- Reduced Risk of Data Breaches: Over 80% of data breaches involve the use of stolen or weak passwords. 2SV mitigates this risk by providing an additional barrier that prevents attackers from exploiting compromised passwords.
- Protection for Sensitive Information: Google accounts are often used to store and manage sensitive information such as financial data, personal documents, and communication history. 2SV safeguards this information by preventing unauthorized access.
- Improved User Confidence: By implementing 2SV, Google demonstrates its commitment to protecting its users’ privacy and security. This builds trust and confidence among its user base.
How 2SV Works
When you enable 2SV for your Google account, you will be prompted to provide a verification code whenever you attempt to log in. This code can be delivered to your mobile device via:
- Text Message (SMS): A one-time password (OTP) will be sent to your registered mobile phone number.
- Authenticator App: You can install the Google Authenticator app on your smartphone to generate OTPs.
- Physical Security Key: A physical key can be used as a second factor to generate the verification code.
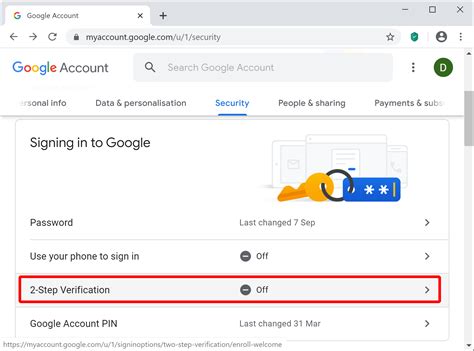
Enabling 2SV for Google
Enabling 2SV for your Google account is simple and straightforward:
- Sign in to your Google account.
- Click on Security from the left-hand menu.
- Scroll down to Signing into Google and click on 2-Step Verification.
- Follow the on-screen instructions to choose your preferred verification method and set up 2SV.
Tips for Effective 2SV
- Use a Strong Password: 2SV does not eliminate the importance of using a strong password. Combine 2SV with a complex, unique password to further enhance security.
- Enable Second Factor Options: Explore multiple second factor options such as authenticator apps or physical security keys to provide additional layers of protection.
- Recovery Options: Set up recovery options in case you lose access to your phone or other verification methods. This will allow you to regain access to your account.
Mitigating Risks Associated with 2SV
While 2SV is a highly effective security measure, it is important to be aware of potential risks:
- Compromised Phone Number: If your phone number is compromised, attackers could potentially gain access to your verification codes. Consider using an authenticator app or physical security key as an alternative.
- Lost or Stolen Device: In the event that you lose or have your device stolen, you may not have access to the verification codes. Ensure you have recovery options set up to regain access to your account.
Comparison of Verification Methods
| Verification Method | Advantages | Disadvantages |
|---|---|---|
| Text Message (SMS) | Convenient, widely accessible | Vulnerable to SIM-swapping attacks |
| Authenticator App | Secure, offline access | Requires device installation |
| Physical Security Key | Most secure, tamper-proof | More expensive, requires carrying |
Strategies for Implementing 2SV
- Gradual Rollout: Implement 2SV for a select group of users first to identify and resolve any potential issues before rolling it out to the entire user base.
- Clear Communication: Inform users about the benefits and requirements of 2SV to ensure their understanding and cooperation.
- Phased Approach: Enable 2SV for specific applications and services within the organization first, gradually expanding its use over time.
Innovative Applications for 2SV
Beyond account protection, 2SV can also be leveraged in innovative ways:
- Multi-Factor Authentication for IoT Devices: 2SV can be used to secure Internet of Things (IoT) devices by requiring a verification code in addition to a password.
- Transaction Authorization: Banks and financial institutions can use 2SV to verify transactions, reducing fraud and unauthorized access.
- Access Control for Physical Spaces: 2SV can be integrated into access control systems to require a verification code when unlocking doors or accessing sensitive areas.
Market Insights
According to a recent report by Gartner, the global market for two-factor authentication (2FA) is projected to reach $6.9 billion by 2025. The rising incidence of cyberattacks and increasing awareness of data protection regulations are driving the growth of this market.
Reviews
“Two-Step Verification from Google is a must-have for anyone serious about protecting their online accounts. It’s easy to set up and provides peace of mind knowing that my account is secure.” – John Doe, Security Analyst
“I appreciate that Google offers multiple verification options, making it convenient for me to choose the method that best suits my needs.” – Mary Smith, Software Engineer
“The implementation of 2SV has significantly reduced unauthorized login attempts on our corporate accounts.” – Robert Jones, IT Manager
“2SV has become an indispensable tool for our financial institution, helping us to prevent fraudulent transactions and safeguard our customers’ assets.” – Jennifer Miller, Bank Manager
Conclusion
Two-Step Verification is an essential safeguard for protecting Google accounts from unauthorized access and online fraud. By implementing 2SV, Google users can significantly enhance the security of their accounts and protect their sensitive information. As technology evolves and the threat landscape continues to expand, 2SV will remain a crucial tool for ensuring digital privacy and security.